PCI-DSS Standard stands for „Payment Card Industry Data Security Standard.“ The PCI standard corresponds to a set of rules that reflects the security requirements for payment transactions with credit cards. This standard is binding for all companies, institutions, and organizations that process credit cardholder data.
Companies and organizations that process cardholder data (CHD) electronically on a cardholder environment (CDE) must secure this environment against data abuse and unauthorized access following the PCI guidelines to protect its ongoing operation. Furthermore, the standard provides a clear assignment of responsibilities for the different areas and tasks within the CDE. It must be possible to track all access and work steps. Physical security and the associated processes to ensure this in data center operations are essential to operating such an environment. These requirements concern 12 areas:
- A firewall concept
- Password security
- Protection of cardholder data
- Data encryption
- Anti-virus software
- Systems and application maintenance
- Access restriction
- User-specific access
- Physical access restriction
- Tracking and monitoring data access
- Regular testing (systems and processes
- Maintaining an information security policy
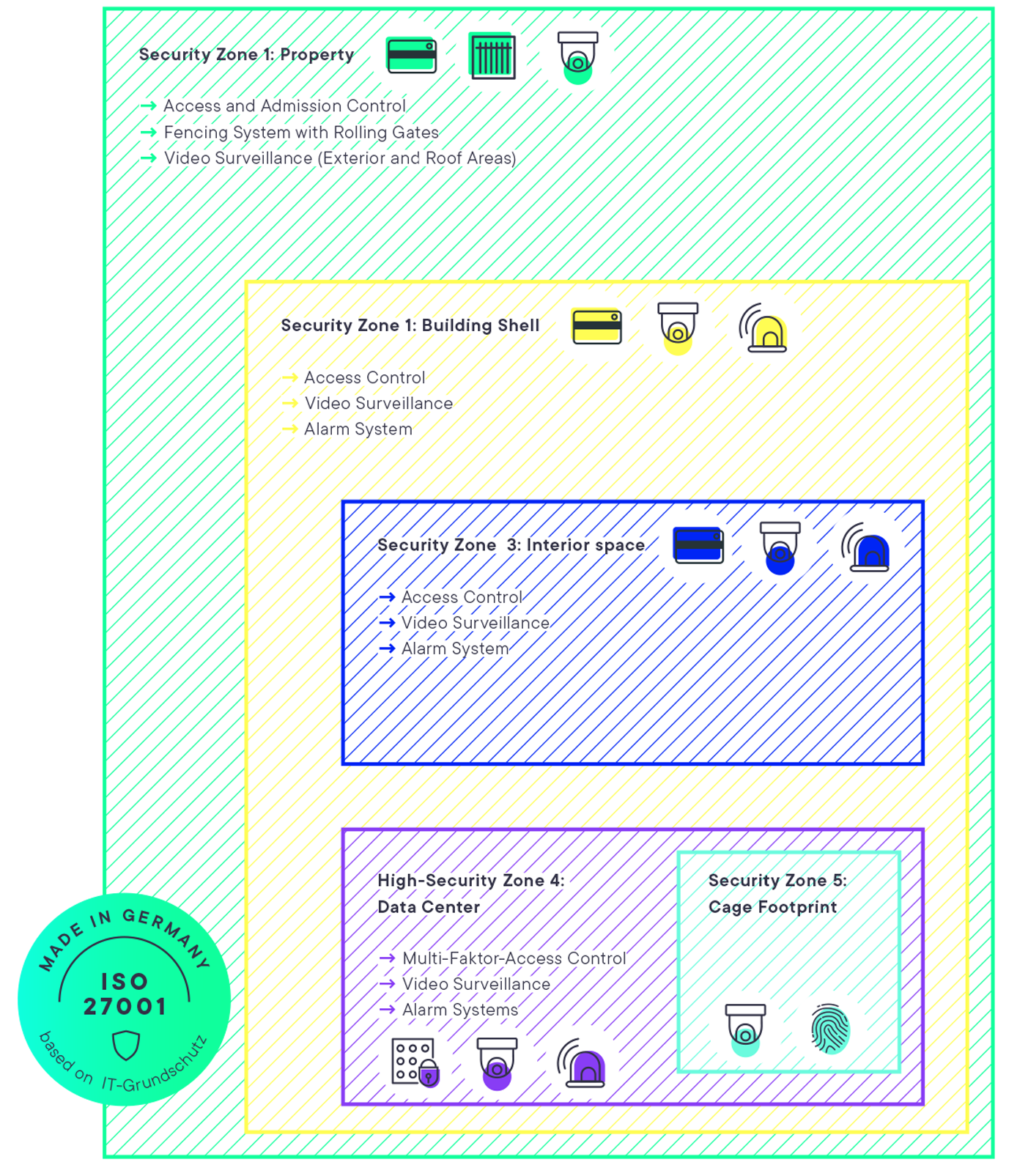
Professional access controls and processes, seamless video surveillance around the clock, logging and exact verification of persons in the data center, data comparison, and plausibility checks ensure that admission and access to the environment are tracked.
As a co-location customer in our data center, you benefit from a service already PCI-certified by a qualified auditor („QSA“), which extends to your rack cabinet. This certification allows you to concentrate on the compliance of your rack-operated infrastructure and refer to the physical security of your rack based on our certification, which covers essential components of requirements 9 and 12 of the PCI requirements catalog and requirement 11.1 regarding wireless access points. These points are no longer included in your audit as you build your certification on the certified PCI compliance of the data center operator.
E-commerce providers, content providers, institutions, and other organizations that offer services or products or accept donations online by credit card, therefore, have the opportunity to implement this in a PCI-certified data center environment in their own, individually lockable 19“ rack (with 22 or 42 height units). We are happy to provide you with our Attestation of Compliance („AOC“) for this purpose.